aws well-architected: fqdn egress filtering
SECURITY PILLAR – FINANCIAL SERVICES INDUSTRY LENS
To quote FSISEC14: Managing data loss prevention (Use Fully Qualified Domain Name (FQDN) ingress and egress filters) from the Security Pillar of the Financial Services Industry Lens in the AWS Well-Architected framework,
Specifying policies by IP may not be practical because domain names can often be translated to many different IP addresses, and maintaining security groups at each egress point can be challenging. Filtering outbound traffic by an expected list of domain names can be an efficient way to secure egress traffic from a VPC because the hostnames of these services are typically known at deployment, and the list of hosts that need to be accessed by an application are not extensive and rarely change.
Filtering traffic by a list of domain names enables companies to centralize the maintenance and deployment of rules. Use a third-party solution to implement highly available, secure FQDN Egress Filtering service.
SECURE FQDN EGRESS FILTERING
The DiscrimiNAT Firewall enables developers and security architects alike in implementing a cloud-native FQDN egress filtering solution.
It enforces internet-bound traffic security by only allowing connections that are TLS 1.2, TLS 1.3 or SSH v2 with bidirectional in-band checks. Present-day HTTPS connections are HTTP encapsulated in at least TLS 1.2. Misconfigured clients or very old server endpoints, i.e. utilising older and now insecure protocols, will have their connections denied through this firewall.
The DiscrimiNAT also conducts out-of-band checks, such as DNS, for robust defence against sophisticated malware and insider threats. Gets your VPC ready for a proper pentest.
AGILITY
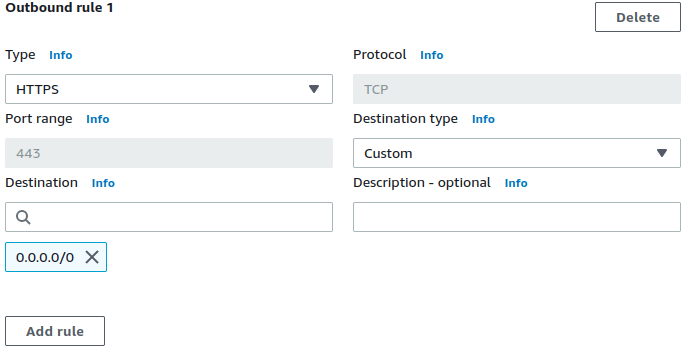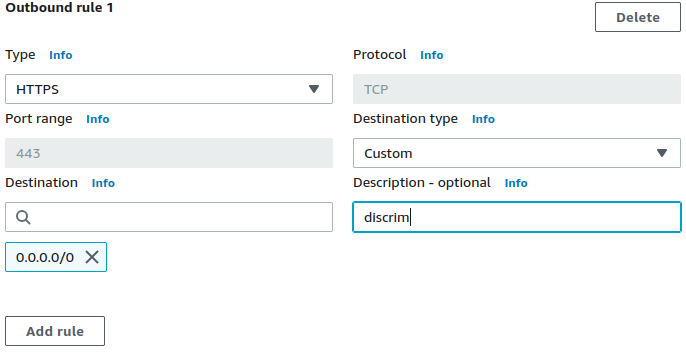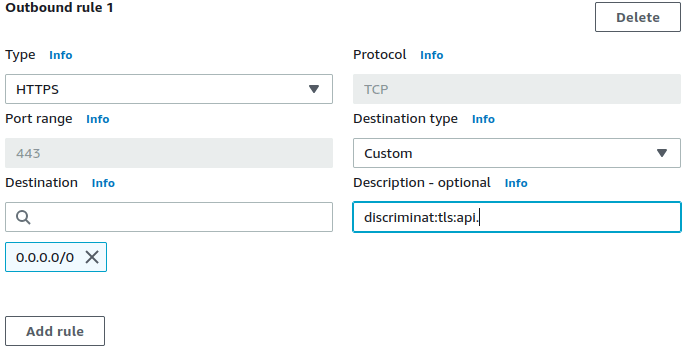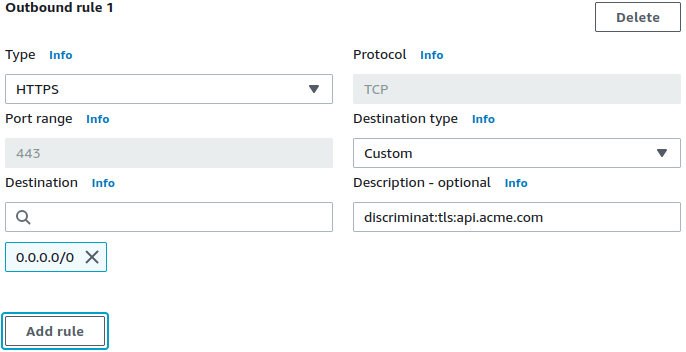
FQDNs of services on the internet are associated with applications right at the Security Groups level, so the maintenance and deployment is in the hands of the same team that deploys the applications. This also allows for granular egress control over multiple applications in the same VPC.
RESILIENCE
An Auto-Scaling Group ensures this firewall, a NAT Gateway replacement, remains highly-available. There are no data processing or transfer charges either. And changes to configuration are logged straight into CloudWatch, as are the flow logs.
See the demo video or proceed to the DiscrimiNAT on AWS page.
Contact our DevSecOps Support for queries at any stage of your journey.