Connecting to MS/Azure SQL Server over TLS
Users may encounter connection errors while connecting to SQL Server 2022 (or greater) with reason set to unsupported protocol in discriminat-flow logs.
Solution: Set Encrypt=strict in the connection string of the SQL Server driver. Check supported driver versions here.
Background
Microsoft uses a protocol called Tabular Data Stream (TDS) to establish connection between a SQL Server driver and a SQL Server. Prior to version 8 of the TDS protocol, TLS encryption was preceded by a cleartext prelogin phase. With TDS version 8, TLS precedes any TDS messages.
The following snippet is taken from a Microsoft document on TDS 8.0:
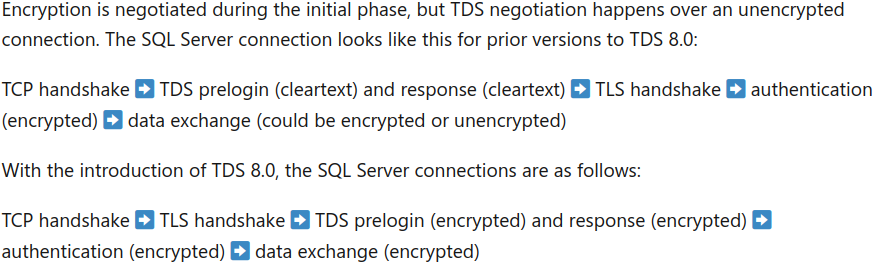
Also from that document:
The TLS handshake now precedes any TDS messages, wrapping the TDS session in TLS to enforce encryption, making TDS 8.0 aligned with HTTPS and other web protocols. This significantly contributes to TDS traffic manageability as standard network appliances are now able to filter and securely passthrough SQL queries.
Solution
It is sufficient to set Encrypt=strict in the connection string. For other methods and application stacks, please see Connect to SQL Server with strict encryption on Microsoft docs.
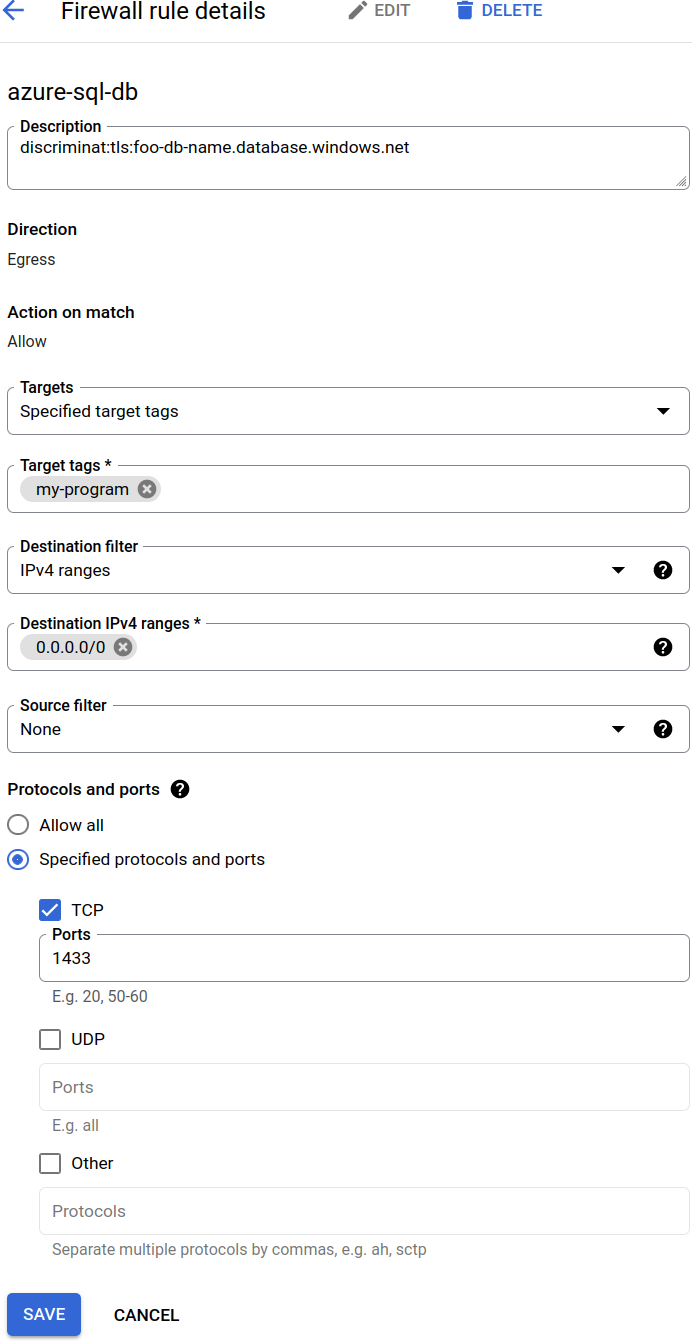
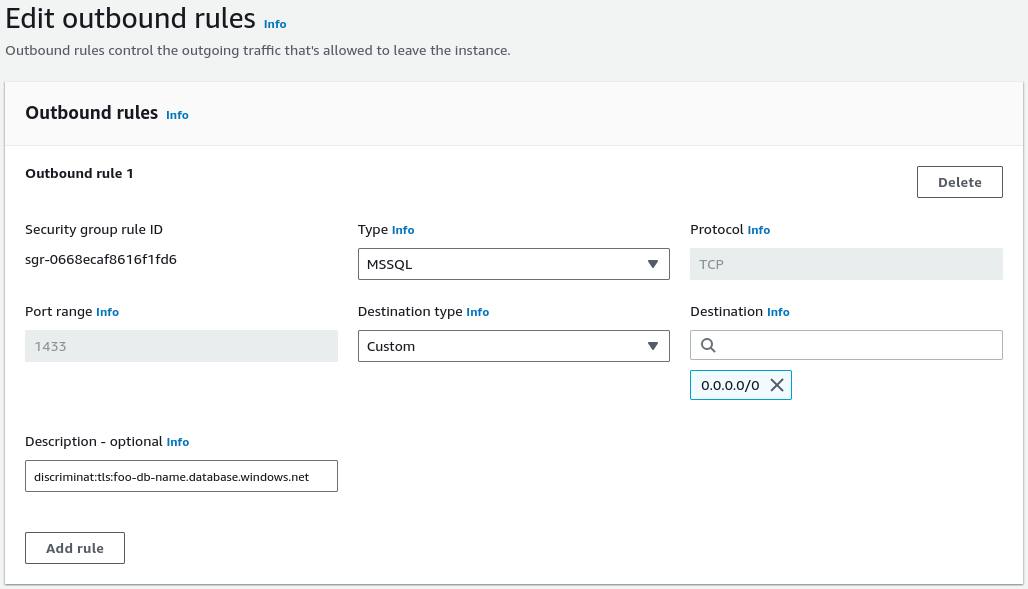
Example Rule Configuration for DiscrimiNAT
The following examples assume TCP port 1433 – which is the default connection port for MS SQL Server and Azure SQL Database.
on AWS
on GCP