Logs Reference
Fields
flow logs
Flow Logs can be found in CloudWatch under the DiscrimiNAT log group, in the flow log stream. A typical flow log looks like:
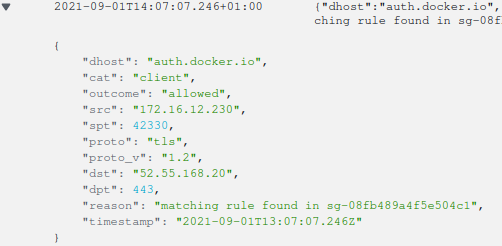
Here's a summary of the possible fields:
dhost: destination hostname/FQDN or IP Address
cat: packet origin – client or server
outcome: allowed or disallowed
src: source IP address
spt: source port
proto: tls, ssh, http or unknown protocol
proto_v: version of the identified protocol
dst: destination IP address
dpt: destination port
reason: reason for the outcome – such as in which Security Group was a matching protocol rule found, cache not ready yet for a newly discovered allowlist entry, or which protocol anomaly led to the connection being disallowed
instance: the EC2 instance ID of the DiscrimiNAT instance this log line was generated from
If X.509 CRLs are set to be allowed, or if there is some plaintext HTTP egress traffic with requisite outbound ports open, there may be HTTP flow logs with the following fields. Note that HTTP is generally not allowed unless X.509 CRLs were allowed and the requested URL was of a CRL Endpoint.
http_code, http_method, http_path, http_user_agent: these fields can be useful to understand which application the plaintext HTTP traffic is originating from
And if a Security Group with a see-thru rule in it is found attached to a client application, the following fields will be also present:
see_thru_days_remaining: number of days remaining while the see-thru rule will be non-blocking, as defined in the see-thru rule itself
see_thru_gid: the Security Group ID where the see-thru rule was found, or %default if set via preferences
see_thru_exerted: when true, the see-thru rule had to let this connection through and there was no protocol rule that would have allowed it; when false, there was a protocol rule that would have let the connection through anyway and its presence will be identified in the reason field; or the see-thru rule has expired
Watch this 4 minute video to understand these three fields, and their interplay with the outcome field, when viewed in the Cloud web console.
Config reference for the see-thru rules can be found here.
config logs
Config Logs can be found in CloudWatch under the DiscrimiNAT log group, in the config log stream. They form an audit trail of changes made to rules and Security Group attachments as clients come and go.
Here's a summary of the possible fields:
cat: fqdn (addr), wildcard pattern (wildcard-addr), client, see-thru or self change category
outcome: accepted something new in the internal configuration, removed something because it had been removed from external configuration sources, or rejected something (because of reason), or warning about a syntactically correct configuration input but one which wasn't going to work as expected (because of reason)
client: IP address of an affected client
subnet: block of IP addresses in the a.b.c.d/e notation of an affected subnet (mutually exclusive with client)
gid: the Security Group ID that relates to this change
addr: the FQDN, wildcard pattern or IP Address found in a Security Group rule
proto: tls or ssh protocol as identified in the rule
reason: reason for usually a warning or a rejected outcome
instance: the EC2 instance ID of the DiscrimiNAT instance this log line was generated from
If X.509 CRLs are set to be allowed there will be an additional field:
http_path: the document path over HTTP for CRL data
And if a Security Group with a see-thru rule in it is found attached to a client application, there will be an additional field:
thru_date: the date until which the non-blocking see-thru mode should remain effective; past this date such a rule would lose effect
Filters
The log lines are JSON-structured so each field can be addressed specifically. More of CloudWatch syntax can be explored on its Filter and pattern syntax page.
disallowed connections
{ $.outcome = "disallowed" }
allowed but protocol is not TLS
{ $.outcome = "allowed" && $.proto != "tls" }
connections from a specific client where the destination host is not api.github.com
{ $.cat = "client" && $.src = "172.16.1.9" && $.dhost != "api.github.com" }
security groups where the see-thru mode exception has only 2 or less days left
{ $.see_thru_days_remaining <= 2 }
connections where the see-thru mode had to be used, but not for perhaps telemetry data
{ $.see_thru_exerted is true && $.dhost != "ec2-instance-connect.*" }
Recipes
building an allowlist from scratch (video version)
Watch this 3½ minute video to build the allowlists super quick! The two commands used in the video are also documented here, underneath the video.
Command 1:
aws logs filter-log-events --output json --no-paginate --log-group-name DiscrimiNAT --log-stream-names flow --filter-pattern '{$.dhost != "" && $.see_thru_gid = '$SECURITY_GROUP_ID' && $.see_thru_exerted is true}' --start-time $(date --date '2 hours ago' +%s000) | jq '[.events[].message | fromjson]' | dd of=frequency-fqdns.json
Command 2:
cat frequency-fqdns.json | jq --raw-output 'group_by(.dhost) | map(.[0] + {"count": length}) | sort_by(.count) | reverse | [.[].dhost] | @csv' | tr --delete '"'
building an allowlist from scratch (text version)
This method is now deprecated in favour of the CloudShell based method above.
Create a new Security Group, with a
see-thrurule in it. See the config reference and an example here. Give it a thru date sufficient enough to capture all stages of the application's lifecycle, such as deployment, restart, the occassional uploading of reports, telemetry, monitoring, etc. Note the Security Group ID.Attach this Security Group to the application. In AWS this could be either attaching the Security Group to the EC2 instances in addition to other attachments, or in the case of serverless workloads, to the Network Interface (ENI) that is in the VPC.
Let the application follow its normal course of lifecycle. This could last a few hours, days or weeks depending on the application.
Go to CloudWatch Log Insights and select the DiscrimiNAT log group. Then enter the following query, select an appropriate time range, and run it. Note: You'll have to replace the Security Group ID in this example with the one that was created above.
filter see_thru_exerted AND see_thru_gid = "sg-00replaceme00"
| stats count() by see_thru_exerted, see_thru_gid, dhost, proto, dpt
This will produce a table of results like:
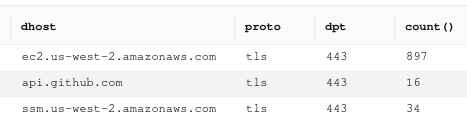
- From the information in the results table, specific allowlist protocol rules can be created. For example:
discriminat:tls:ec2.us-west-2.amazonaws.com,ssm.us-west-2.amazonaws.com
and discriminat:tls:api.github.com with protocol TCP and destination port 443.
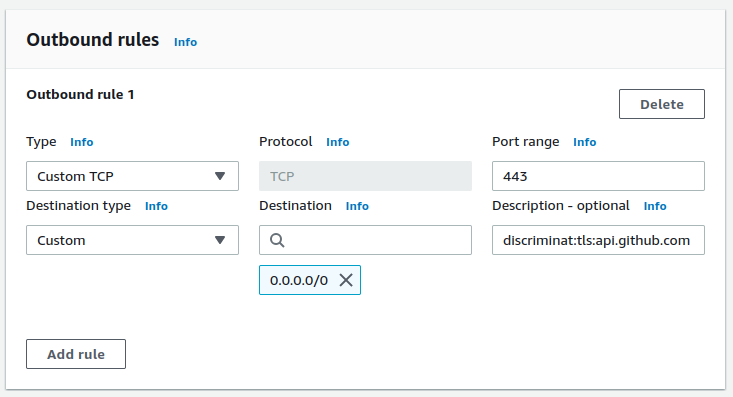
Full reference for creating these protocol rules is here.
Once these protocol rules are attached to the application, run the full application lifecycle again, and then the query at #4 to ensure that
see_thru_exerteddid not have to be used to let any disallowed traffic through. There may be the case where you choose to disallow certain destinations anyway, such as endpoints that just collect telemetry data.Detach or remove the
see-thrurule from the application and give it another full lifecycle run to ensure it works smoothly.