Reference Architectures
The DiscrimiNAT Firewall supports three deployment topologies. You are free, however, to deploy it as you see fit and consult our DevSecOps Support as needed.
In a Shared VPC setup, DiscrimiNAT must be deployed in the VPC Owner account.
The key differentiators between the topologies are laid out in the table below.
| Topology | Failure Time to Detection | Failure Time to Recovery | Min Instances per AZ | Inter-AZ Data Transfer | Auto Scaling |
|---|---|---|---|---|---|
| GWLB in Cross-Zone | 10 seconds | 60 seconds† | 1 | yes | yes |
| GWLB in Intra-Zone | 10 seconds | 60 seconds† | 2 | no | yes |
| ENI per AZ | 2 seconds | 150 seconds‡ | 1 (also max) | no | no |
† This is GWLB behaviour as quoted below. The health checks' interval, though, is set to 5 seconds in our Terraform modules therefore reducing the 20-second delay from them to 10 seconds.
The minimum duration to start re-routing new flow is up to 70 seconds. It is a sum of 20 seconds for health checks (Min. Interval: 10s, Min. threshold: 2) and 50 seconds for GWLB backend to detect and re-route. Source: https://aws.amazon.com/.../best-practices-for-deploying-gateway-load-balancer/
‡ In practice, this is how long EC2 Auto Scaling takes to replace a DiscrimiNAT Instance upon receiving Unhealthy HealthStatus on the SetInstanceHealth API. The GWLB topologies do not use the SetInstanceHealth API for recovery, but instead are purely load balancer health check managed.
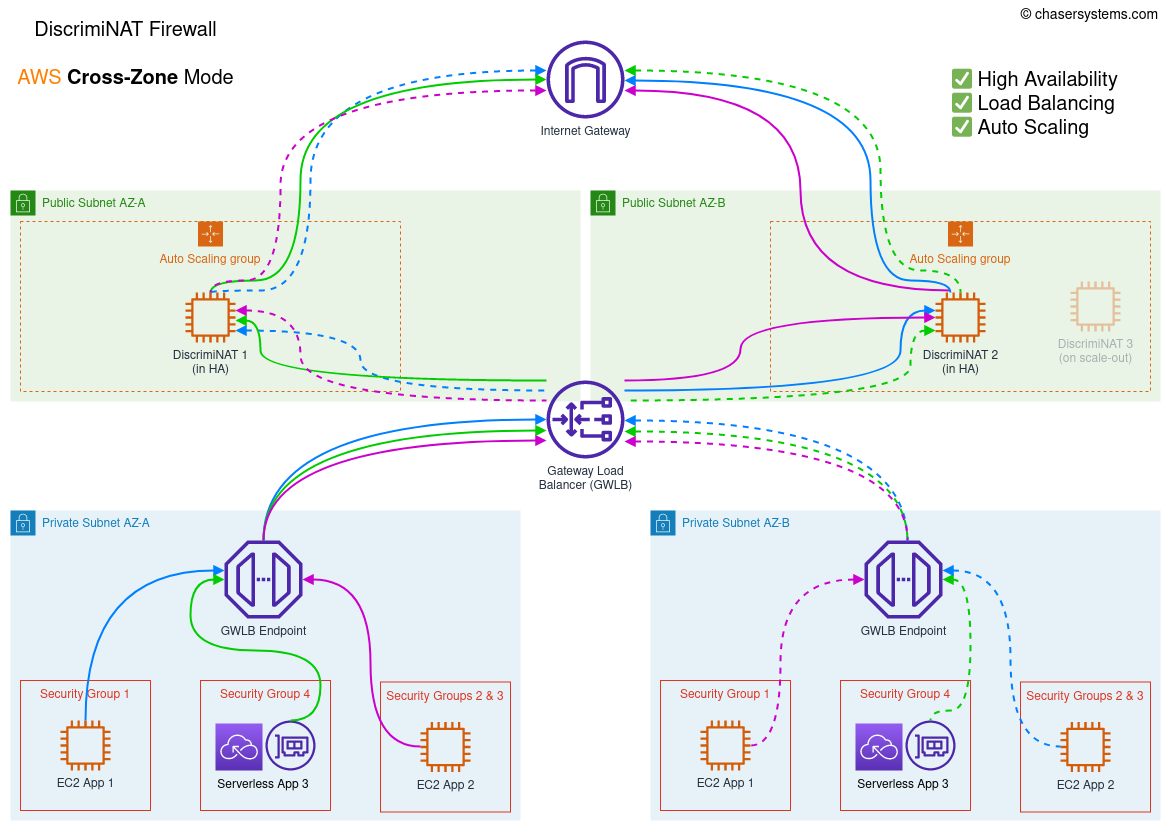
GWLB in Cross-Zone mode
In the cross-zone mode, the Gateway Load Balancer (GWLB) will distribute traffic evenly across all deployed AZs. This reduces the number of DiscrimiNAT Firewall instances you will have to run for high-availability but increases data-transfer costs.
Terraform variable high_availability_mode should be set to cross-zone. This is also the default. The Terraform module is here.
Minimum number of allocated Elastic IPs for high-availability (=2) with headroom for auto-scaling (+1) is 3 per region.
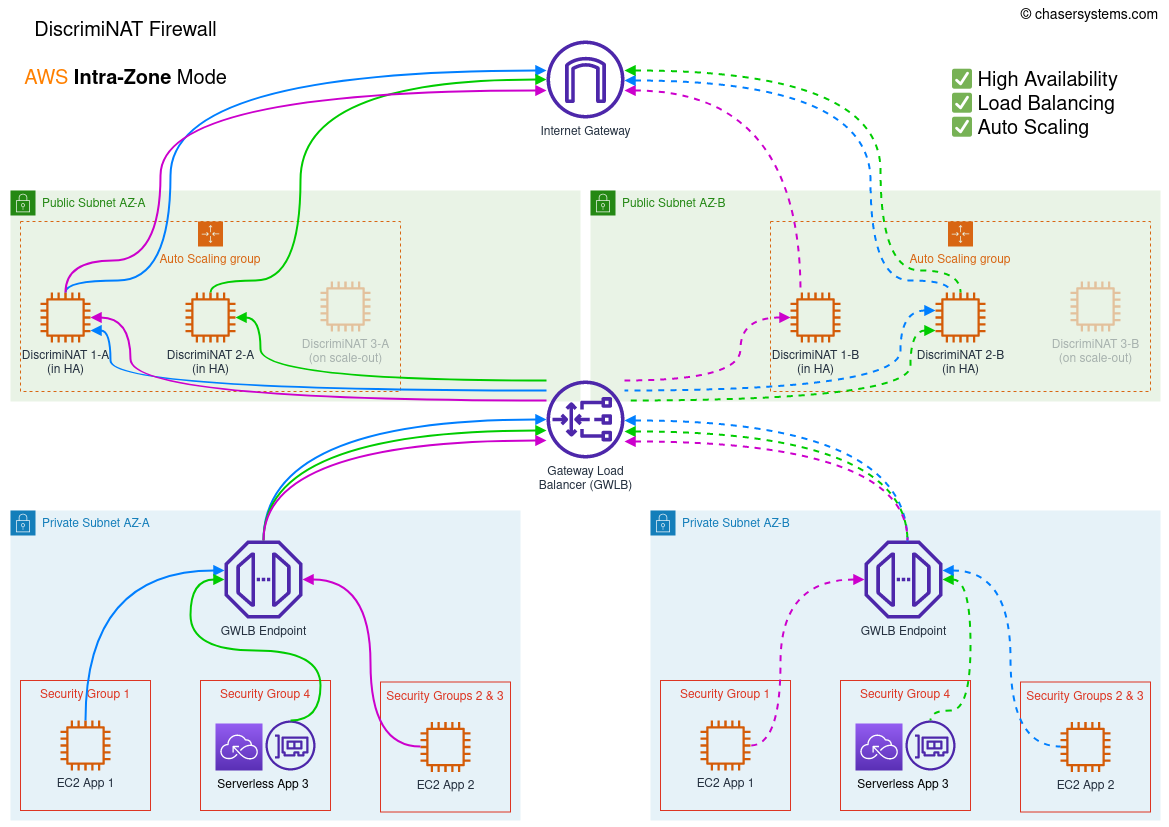
GWLB in Intra-Zone mode
In the intra-zone mode, the GWLB will distribute traffic evenly across all DiscrimiNAT Firewall instances in the same AZ as the client. For effective high-availability, this mode will need at least two instances per deployed AZ. Please note this does not fully protect you against the failure of an entire AZ on the Amazon side, however your other services in the zone would potentially be impacted too and therefore not sending egress traffic.
Terraform variable high_availability_mode should be set to intra-zone. The Terraform module is here.
Traffic will not be balanced to other zones, even in case of failure of all instances in one zone, therefore minimum high-availability numbers (=2) have to be configured per AZ.
Minimum number of allocated Elastic IPs for high-availability (=2) with headroom for auto-scaling (+1) is 3 per AZ; and therefore 6 for two AZs.
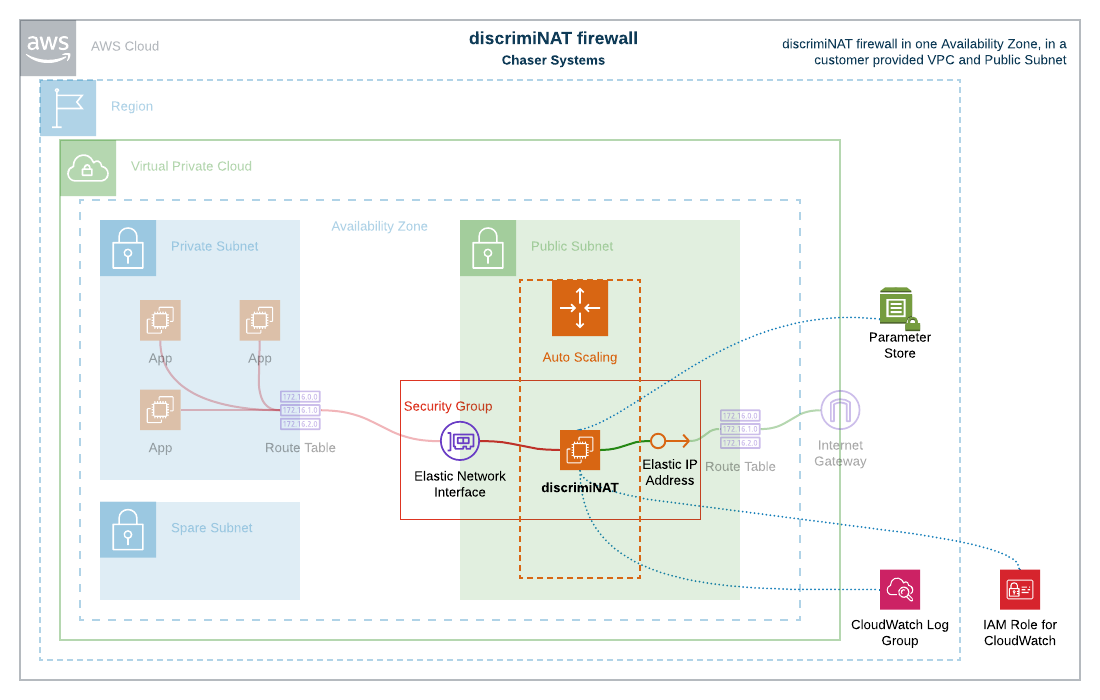
ENI per AZ
A single DiscrimiNAT instance, wrapped in an Auto Scaling Group of its own, is deployed per AZ without any load balancers. Routing is directly to the ENI (Network Interface) of this instance. The ENI is statically bound to the Launch Template in the provided CloudFormation & Terraform modules, therefore only one active instance per AZ can exist at a time. Should the built-in health check fail, the instance will be terminated and a new one brought in its place by its Auto Scaling Group. This process takes up to 150 seconds.
The Terraform module for this topology is here.