Serverless VPC Access Connectors
Concepts
Serverless VPC Access makes it possible for you to connect directly to your Virtual Private Cloud network from serverless environments such as Cloud Run, App Engine, or Cloud Functions.
Source: https://docs.cloud.google.com/vpc/docs/serverless-vpc-access
From v2.4 onwards, the DiscrimiNAT supports filtering traffic egressing from Serverless VPC Access Connectors.
Network tags
The network tags on Firewall Rules that apply to Serverless VPC Access Connectors have preset names defined by Google Cloud Platform.
Serverless VPC Access network tags let you refer to VPC connectors in firewall rules and routes.
Every Serverless VPC Access connector automatically receives two network tags (sometimes called instance tags):
- Universal network tag:
vpc-connectorApplies to all existing connectors and any connectors made in the future- Unique network tag:
vpc-connector-REGION-CONNECTOR_NAMEApplies to the connectorCONNECTOR_NAMEinREGIONThese network tags cannot be deleted. New network tags cannot be added.
Source: https://docs.cloud.google.com/vpc/docs/serverless-vpc-access#network-tags
Examples
- For a connector named
fooineurope-west2region, the network tag applicable to just the traffic from this connector will bevpc-connector-europe-west2-foo. - The network tag applicable to all connectors, regardless of name or region, will be
vpc-connector.
Requirements
Serverless
The egress settings of the serverless platform need to be configured to send all traffic through a connector rather than just the traffic to internal addresses. This is accomplished during the setup of the serverless workload, and in the following ways.
- Cloud Run
- Cloud Functions
- App Engine
Route all traffic through the VPC connector when selecting a connector.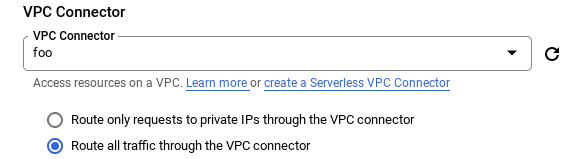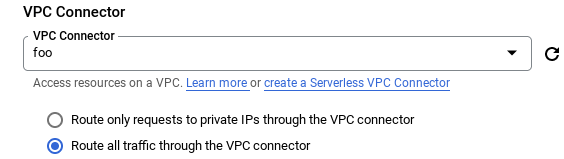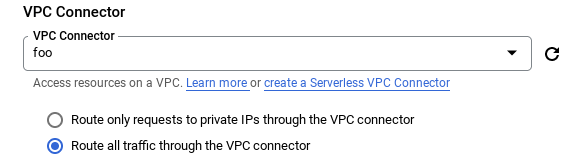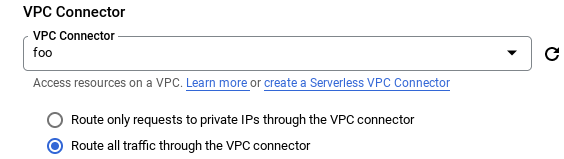
Reference: https://docs.cloud.google.com/run/docs/configuring/connecting-vpc#connectors
Route all traffic through the VPC connector under Egress settings.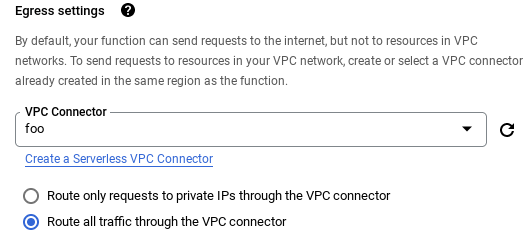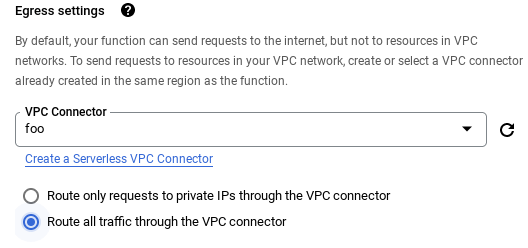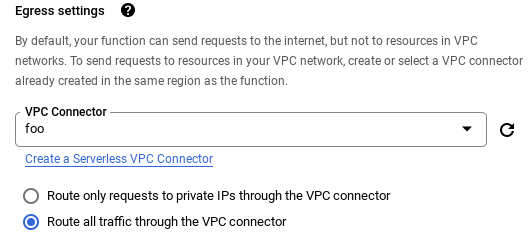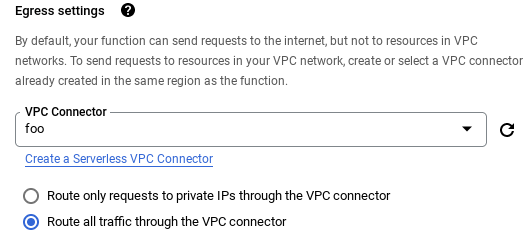
Reference: https://docs.cloud.google.com/run/docs/configuring/networking-best-practices#direct-vpc-throughput
egress_settings property to all-traffic.vpc_access_connector:
name: projects/PROJECT_ID/locations/REGION/connectors/CONNECTOR_NAME
egress_setting: all-traffic
Reference: https://docs.cloud.google.com/appengine/docs/standard/connecting-vpc#egress
Firewall Rules
Firewall Rules from NAT Ranges and Health Check Ranges, as described at ¹, must be created for the VPC Connectors.
Additionally, firewall rules to allow connections from serverless workloads to DiscrimiNAT instances would have to be created. If using Terraform, the variable client_cidrs accepts a list of IP ranges for this. The subnets allocated for VPC Connectors should be added to this list.
¹ https://docs.cloud.google.com/vpc/docs/configure-serverless-vpc-access#restrict-access
Role
The following permissions must be added to the Role meant to be granted to the service account for DiscrimiNAT instances, in order for it to be able to pick up the connector subnets:
vpcaccess.connectors.list
compute.subnetworks.get
If Serverless VPC Access Connectors are deployed in Service Projects of a Shared VPC , see the Shared VPC setup page and grant permissions as discussed in the Service Account page.